- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- Phrack Magazine: Digital hacking magazine.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
martes, 30 de junio de 2020
10 Useful Websites for Hackers 2018
jueves, 11 de junio de 2020
OWASP ZAP RELEASES V2.8.0 WITH THE HEADS UP DISPLAY
OWASP ZAP RELEASES V2.8.0 WITH THE HEADS UP DISPLAY
Heads Up Display simplifies and improves vulnerability testing for developers
London, England, 20 June 2019. OWASP™ ZAP (Open Web Application Security Project™ Zed Attack Proxy) has released a new version of its leading ZAP Project which now includes an innovative Heads Up Display (HUD) bringing security information and functionality right into the browser. Now software developers can interactively test the reliability and security of their applications in real time while controlling a wide variety of features designed to test the quality of their software.
ZAP is a free, easy to use integrated penetration testing tool. With the addition of the Heads Up Display, ZAP can be used by security professionals and developers of all skill levels to quickly and more easily find security vulnerabilities in their applications. Given the unique and integrated design of the Heads Up Display, developers and functional testers who might be new to security testing will find ZAP an indispensable tool to build secure software.
The latest version of ZAP can be downloaded from https://www.owasp.org/index.
In addition to being the most popular free and open source security tools available, ZAP is also one of the most active with hundreds of volunteers around the globe continually improving and enhancing its features. ZAP provides automated scanners as well as a set of tools that allows new users and security professionals to manually identify security vulnerabilities. ZAP has also been translated into over 25 languages including French, Italian, Dutch, Turkish and Chinese.
Simon Bennetts, OWASP ZAP Project Leader commented: "This is a really important release for the project team and developers who want to build great and secure applications. The HUD is a completely new interface for ZAP and one that is unique in the industry. It shows that open source projects continue to create high-quality, new and exciting tools that deliver real value to the market - and at no cost to users."
"ZAP is the Foundation's most popular software tool," said Mike McCamon interim executive director of the OWASP Foundation. McCamon continued, "For nearly two decades OWASP continues to be a great destination for innovators to host, develop, and release software that will secure the web. Simon and the entire ZAP community deserves great recognition for their continued devotion to open source excellence."
For further information please contact:
Simon Bennetts, OWASP ZAP Project Leader: simon.bennetts@owasp.org or Mike McCamon, Interim Executive Director, mike.mccamon@owasp.com
Heads Up Display simplifies and improves vulnerability testing for developers
London, England, 20 June 2019. OWASP™ ZAP (Open Web Application Security Project™ Zed Attack Proxy) has released a new version of its leading ZAP Project which now includes an innovative Heads Up Display (HUD) bringing security information and functionality right into the browser. Now software developers can interactively test the reliability and security of their applications in real time while controlling a wide variety of features designed to test the quality of their software.
ZAP is a free, easy to use integrated penetration testing tool. With the addition of the Heads Up Display, ZAP can be used by security professionals and developers of all skill levels to quickly and more easily find security vulnerabilities in their applications. Given the unique and integrated design of the Heads Up Display, developers and functional testers who might be new to security testing will find ZAP an indispensable tool to build secure software.
The latest version of ZAP can be downloaded from https://www.owasp.org/index.
In addition to being the most popular free and open source security tools available, ZAP is also one of the most active with hundreds of volunteers around the globe continually improving and enhancing its features. ZAP provides automated scanners as well as a set of tools that allows new users and security professionals to manually identify security vulnerabilities. ZAP has also been translated into over 25 languages including French, Italian, Dutch, Turkish and Chinese.
Simon Bennetts, OWASP ZAP Project Leader commented: "This is a really important release for the project team and developers who want to build great and secure applications. The HUD is a completely new interface for ZAP and one that is unique in the industry. It shows that open source projects continue to create high-quality, new and exciting tools that deliver real value to the market - and at no cost to users."
"ZAP is the Foundation's most popular software tool," said Mike McCamon interim executive director of the OWASP Foundation. McCamon continued, "For nearly two decades OWASP continues to be a great destination for innovators to host, develop, and release software that will secure the web. Simon and the entire ZAP community deserves great recognition for their continued devotion to open source excellence."
For further information please contact:
Simon Bennetts, OWASP ZAP Project Leader: simon.bennetts@owasp.org or Mike McCamon, Interim Executive Director, mike.mccamon@owasp.com
Related links
miércoles, 10 de junio de 2020
C++ Std::String Buffer Overflow And Integer Overflow
Interators are usually implemented using signed integers like the typical "for (int i=0; ..." and in fact is the type used indexing "cstr[i]", most of methods use the signed int, int by default is signed.
Nevertheless, the "std::string::operator[]" index is size_t which is unsigned, and so does size(), and same happens with vectors.
Besides the operator[] lack of negative index control, I will explain this later.
Do the compilers doesn't warn about this?
If his code got a large input it would index a negative numer, let see g++ and clang++ warnings:
No warnings so many bugs out there...
In order to reproduce the crash we can load a big string or vector from file, for example:
I've implemented a loading function, getting the file size with tellg() and malloc to allocate the buffer, then in this case used as a string.
Let see how the compiler write asm code based on this c++ code.
So the string constructor, getting size and adding -2 is clear. Then come the operator<< to concat the strings.
Then we see the operator[] when it will crash with the negative index.
In assembly is more clear, it will call operator[] to get the value, and there will hapen the magic dereference happens. The operator[] will end up returning an invalid address that will crash at [RAX]
In gdb the operator[] is a allq 0x555555555180 <_znst7__cxx1112basic_stringicst11char_traitsicesaiceeixem plt="">
(gdb) i r rsi
rsi 0xfffffffffffefffe -65538
The implmementation of operator ins in those functions below:
(gdb) bt
#0 0x00007ffff7feebf3 in strcmp () from /lib64/ld-linux-x86-64.so.2
#1 0x00007ffff7fdc9a5 in check_match () from /lib64/ld-linux-x86-64.so.2
#2 0x00007ffff7fdce7b in do_lookup_x () from /lib64/ld-linux-x86-64.so.2
#3 0x00007ffff7fdd739 in _dl_lookup_symbol_x () from /lib64/ld-linux-x86-64.so.2
#4 0x00007ffff7fe1eb7 in _dl_fixup () from /lib64/ld-linux-x86-64.so.2
#5 0x00007ffff7fe88ee in _dl_runtime_resolve_xsavec () from /lib64/ld-linux-x86-64.so.2
#6 0x00005555555554b3 in main (argc=2, argv=0x7fffffffe118) at main.cpp:29
29 cout << "penultimate byte is " << hex << s[i] << endl;
(gdb)
What about negative indexing in std::string::operator[] ?
It's exploitable!
In a C char array is known that having control of the index, we can address memory.
Let's see what happens with C++ strings:
The operator[] function call returns the address of string plus 10, and yes, we can do abitrary writes.
Note that gdb displays by default with at&t asm format wich the operands are in oposite order:
And having a string that is in the stack, controlling the index we can perform a write on the stack.
To make sure we are writing outside the string, I'm gonna do 3 writes:
See below the command "i r rax" to view the address where the write will be performed.
The beginning of the std::string object is 0x7fffffffde50.
Write -10 writes before the string 0x7fffffffde46.
And write -100 segfaults because is writting in non paged address.
So, C++ std::string probably is not vulnerable to buffer overflow based in concatenation, but the std::string::operator[] lack of negative indexing control and this could create vulnerable and exploitable situations, some times caused by a signed used of the unsigned std::string.size()
Nevertheless, the "std::string::operator[]" index is size_t which is unsigned, and so does size(), and same happens with vectors.
Besides the operator[] lack of negative index control, I will explain this later.
Do the compilers doesn't warn about this?
If his code got a large input it would index a negative numer, let see g++ and clang++ warnings:
No warnings so many bugs out there...
In order to reproduce the crash we can load a big string or vector from file, for example:
I've implemented a loading function, getting the file size with tellg() and malloc to allocate the buffer, then in this case used as a string.
Let see how the compiler write asm code based on this c++ code.
So the string constructor, getting size and adding -2 is clear. Then come the operator<< to concat the strings.
Then we see the operator[] when it will crash with the negative index.
In assembly is more clear, it will call operator[] to get the value, and there will hapen the magic dereference happens. The operator[] will end up returning an invalid address that will crash at [RAX]
In gdb the operator[] is a allq 0x555555555180 <_znst7__cxx1112basic_stringicst11char_traitsicesaiceeixem plt="">
(gdb) i r rsi
rsi 0xfffffffffffefffe -65538
The implmementation of operator ins in those functions below:
(gdb) bt
#0 0x00007ffff7feebf3 in strcmp () from /lib64/ld-linux-x86-64.so.2
#1 0x00007ffff7fdc9a5 in check_match () from /lib64/ld-linux-x86-64.so.2
#2 0x00007ffff7fdce7b in do_lookup_x () from /lib64/ld-linux-x86-64.so.2
#3 0x00007ffff7fdd739 in _dl_lookup_symbol_x () from /lib64/ld-linux-x86-64.so.2
#4 0x00007ffff7fe1eb7 in _dl_fixup () from /lib64/ld-linux-x86-64.so.2
#5 0x00007ffff7fe88ee in _dl_runtime_resolve_xsavec () from /lib64/ld-linux-x86-64.so.2
#6 0x00005555555554b3 in main (argc=2, argv=0x7fffffffe118) at main.cpp:29
Then crashes on the MOVZX EAX, byte ptr [RAX]
Program received signal SIGSEGV, Segmentation fault.
0x00005555555554b3 in main (argc=2, argv=0x7fffffffe118) at main.cpp:2929 cout << "penultimate byte is " << hex << s[i] << endl;
(gdb)
What about negative indexing in std::string::operator[] ?
It's exploitable!
In a C char array is known that having control of the index, we can address memory.
Let's see what happens with C++ strings:
The operator[] function call returns the address of string plus 10, and yes, we can do abitrary writes.
Note that gdb displays by default with at&t asm format wich the operands are in oposite order:
And having a string that is in the stack, controlling the index we can perform a write on the stack.
To make sure we are writing outside the string, I'm gonna do 3 writes:
The beginning of the std::string object is 0x7fffffffde50.
Write -10 writes before the string 0x7fffffffde46.
And write -100 segfaults because is writting in non paged address.
So, C++ std::string probably is not vulnerable to buffer overflow based in concatenation, but the std::string::operator[] lack of negative indexing control and this could create vulnerable and exploitable situations, some times caused by a signed used of the unsigned std::string.size()
Related word
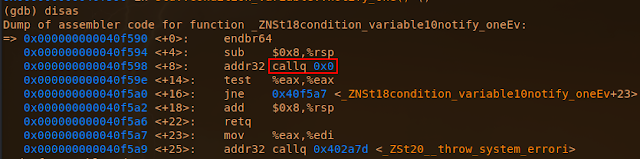
C++ Std::Condition_Variable Null Pointer Derreference
This story is about a bug generated by g++ and clang compilers (at least)
The condition_variables is a feature on the standard library of c++ (libstdc++), when its compiled statically a weird asm code is generated.
Any example on the link below will crash if its compiled statically:
https://en.cppreference.com/w/cpp/thread/condition_variable
In this case the condition_variable.wait() crashed, but this happens with other methods, a simple way to trigger it:
If this program is compiled dynamically the crash doesn't occur:
Looking the dissasembly there is a surprise created by the compiler:
Compilers:
g++ 9.2.1+20200130-2
clang++ v9
Both compilers are generating the "call 0x00"
If we check this call in a dynamic compiled:
The implementation of condition_variable in github:
https://github.com/gcc-mirror/gcc/blob/b7c9bd36eaacac42631b882dc67a6f0db94de21c/libstdc%2B%2B-v3/include/std/condition_variable
The compilers can't copile well this code in static, and same happens on other condition_variable methods.
I would say the _lock is being assembled improperly in static, is not exacly a null pointer derreference but the effects are the same, executing code at address 0x00 which on linux is a crash on most of cases.
Related news
- Pentest Training
- Hacking Process
- Hacker Forum
- Pentestmonkey
- Hacking Names
- Pentesting And Ethical Hacking
- Hacker Keyboard
- Pentest Framework
- Pentest Smtp
- Pentest Practice
- Hacking The System
- Pentest Services
- Pentest Practice Sites
- Pentest Active Directory
- Hacking Names
- Pentest Framework
- Hacking Bluetooth
- Hacking Tutorials
- Pentest Process
RED_HAWK: An Information Gathering, Vulnerability Scanning And Crawling Tool For Hackers
About RED_HAWK: RED_HAWK is a all in one tool for Information Gathering, Vulnerability Scanning and Crawling. A must have tool for all pentesters and hackers.
RED_HAWK's features:
- Basic ScanSite Title (NEW):
IP Address
Web Server Detection IMPROVED
CMS Detection
Cloudflare Detection
robots.txt Scanner - Whois Lookup (IMPROVED)
- Geo-IP Lookup
- Grab Banners IMPROVED
- DNS Lookup
- Subnet Calculator
- Nmap Port Scan
- Sub-Domain Scanner IMPROVED:
Sub Domain
IP Address - Reverse IP Lookup and CMS Detection IMPROVED:
Hostname
IP Address
CMS - Error Based SQLi Scanner
- Bloggers View NEW
HTTP Response Code
Site Title
Alexa Ranking
Domain Authority
Page Authority
Social Links Extractor
Link Grabber - WordPress Scan NEW
Sensitive Files Crawling
Version Detection
Version Vulnerability Scanner - Crawler
- MX Lookup NEW
- Scan For Everything - The Old Lame Scanner
List of CMS Supported on RED_HAWK
RED_HAWK's CMS Detector currently is able to detect the following CMSs (Content Management Systems) in case the website is using some other CMS, Detector will return could not detect.
- WordPress
- Joomla
- Drupal
- Magento
RED_HAWK Installation
How To Configure RED HAWK with moz.com for Bloggers View Scan?
How to use RED_HAWK?
Known Issues of RED_HAWK
ISSUE: Scanner Stops Working After Cloudflare Detection!
SOLUTION: Use the
Watch the video to see how to solve that isuue:
Support and Donations
Found RED_HAWK cool? Well you could buy a cup of tea for the author 😉 Just send any amount of donations (in Bitcoin) to this address: 1NbiQidWWVVhWknsfPSN1MuksF8cbXWCku

Can't donate? well that's no problem just drop a "THANK YOU, AUTHOR" this will motivate me to create more exciting stuffs for you 😉
TODOs for RED_HAWK:
How To Configure RED HAWK with moz.com for Bloggers View Scan?
- Create an account in moz follow this link: Register New Community Account - Moz
- After successful account creation and completing the verification you need to generate the API Keys.
- You can get your API Keys here: https://moz.com/products/mozscape/access.
- Get your AccessID and SecretKey and replace the
$accessIDand$secretKeyvariable's value in theconfig.phpfile
How to use RED_HAWK?
Known Issues of RED_HAWK
ISSUE: Scanner Stops Working After Cloudflare Detection!
SOLUTION: Use the
fix command (for Debian-based distros) or manually install php-curl and php-xml.Watch the video to see how to solve that isuue:
Support and Donations
Found RED_HAWK cool? Well you could buy a cup of tea for the author 😉 Just send any amount of donations (in Bitcoin) to this address: 1NbiQidWWVVhWknsfPSN1MuksF8cbXWCku
Can't donate? well that's no problem just drop a "THANK YOU, AUTHOR" this will motivate me to create more exciting stuffs for you 😉
TODOs for RED_HAWK:
- Make a proper update option ( Installs current version automatically )
- Add more CMS to the detector
- Improve The WordPress Scanner ( Add User, Theme & Plugins Enumeration )
- Create a web version of the scanner
- Add XSS & LFI Scanner
- Improve the Links grabber thingy under bloggers view
- Add some other scans under the Bloggers View
Related posts
Networking | Switching And Routing | Tutorial 1 | 2018
Welcome to my new series of tutorials about networking. Moreover in this series I'll discuss briefly each and every thing related to routing and switching. After that you will able to pass an exam of HCNA, CCNA etc. First of all you have to know which software is used by which company such as Huawei used its own software named eNSP while Cisco used its own software named Cisco Packet Tracer. After that you have to know that how to download and install both of the software in your computer systems. So the purpose of this blog is to give you people an overview about how to download and install both of them.
What is a Network?
First of all we must have to know about what is a network. So the network is the interconnection of two or more than two devices in such a way that they can communicate each other. In computer networks we can say that the interconnection of two or more than two end devices (computer, laptops, printers etc) for the sake of sending and receiving some amount of data is known as computer network.What is Internet?
The very simple and easily understandable definition of a internet is "The network of networks". Now what is meant by that? When different networks from the different areas or at the same areas wanna communicate with each other then internet formed. So we can say that "Internet is the interconnection of different networks in such a way that networks can communicate with each other".Related links
Osueta: A Simple Python Script To Exploit The OpenSSH User Enumeration Timing Attack
About Osueta?
Osueta it's a simple Python 2 script to exploit the OpenSSH User Enumeration Timing Attack, present in OpenSSH versions <= 7.2 and >= 5.*. The script has the ability to make variations of the username employed in the bruteforce attack, and the possibility to establish a DoS condition in the OpenSSH server.
Read more: OpenSSH User Enumeration Time-Based Attack
The bug was corrected in OpenSSH version 7.3.
Authors of Osueta:
- c0r3dump3d: coredump@autistici.org
- rofen: rofen@gmx.de
Osueta's Installation
For Linux users, open your Terminal and enter these commands:
If you're Windows users, follow these steps:
- Install Python 2.7.x from Python.org first. On Install Python 2.7.x Setup, choose Add python.exe to Path.
- Download Osueta-master zip file.
- Then unzip it.
- Open CMD or PowerShell window at the Osueta folder you have just unzipped and enter these commands:
pip install python-nmap paramiko IPypython osueta.py -h
Advice: Like others offensive tools, the authors disclaims all responsibility in the use of this script.
Osueta help menu:
Osueta's examples:
A single user enumeration attempt with username variations:
python2 osueta.py -H 192.168.1.6 -p 22 -U root -d 30 -v yesA single user enumeration attempt with no user variations a DoS attack:
python2 osueta.py -H 192.168.1.6 -p 22 -U root -d 30 -v no --dos yesScanning a C class network with only one user:
python2 osueta.py -H 192.168.1.0/24 -p 22 -U root -v no Scanning a C class network with usernames from a file, delay time 15 seconds and a password of 50000 characters:
python2 osueta.py -H 192.168.1.0/24 -p 22 -L usernames.txt -v yes -d 15 -l 50More articles
- Hackerx
- Pentest Reporting Tool
- Pentest Questions
- Pentest Keys
- Pentest Lab Setup
- Pentest Framework
- Pentest Questions
- Hacking Wifi
- Pentest As A Service
- Pentesting
- Pentest Distro
- Pentest Cheat Sheet
- Pentesting Tools
- Pentest Tools
- Pentest Cyber Security
- Pentest Iso
- Pentest Wifi
- Hacking Books
- Pentest Gear
martes, 9 de junio de 2020
Ophcrack
 " Ophcrack is an open source (GPL license) program that cracks Windows LM hashes using rainbow tables. The program includes the ability to import the hashes from a variety of formats, including dumping directly from the SAM files of Windows. There is also a Live CD version which automates the retrieval, decryption, and cracking of passwords from a Windows system. Rainbow tables for LM hashes of alphanumeric passwords are provided for free by the developers. These tables can crack 99.9% of alphanumeric passwords of up to 14 characters in usually a few seconds, and at most a few minutes. Larger rainbow tables (for LM hashes of passwords with all printable characters, including symbols and space) are available for purchase from Objectif Securité. Starting with version 2.3, Ophcrack also cracks NT hashes. This is necessary if generation of the LM hash is disabled (this is default on Windows Vista), or if the password is longer than 14 characters (in which case the LM hash is not stored)." read more...
" Ophcrack is an open source (GPL license) program that cracks Windows LM hashes using rainbow tables. The program includes the ability to import the hashes from a variety of formats, including dumping directly from the SAM files of Windows. There is also a Live CD version which automates the retrieval, decryption, and cracking of passwords from a Windows system. Rainbow tables for LM hashes of alphanumeric passwords are provided for free by the developers. These tables can crack 99.9% of alphanumeric passwords of up to 14 characters in usually a few seconds, and at most a few minutes. Larger rainbow tables (for LM hashes of passwords with all printable characters, including symbols and space) are available for purchase from Objectif Securité. Starting with version 2.3, Ophcrack also cracks NT hashes. This is necessary if generation of the LM hash is disabled (this is default on Windows Vista), or if the password is longer than 14 characters (in which case the LM hash is not stored)." read more...Website: http://ophcrack.sourceforge.net
Related articles
How To Install Windscribe - The Best Free VPN On GNU/Linux Distros?
Why should you use Windscrive?
Windscribe is well-known for their free VPN service but they also have a paid version. Only with a free account, you will get 10 countries to connect through and change your real IP address and 10GB of free traffic (if you use an email to sign up Windscribe), and unlimited devices.
The Free version is awesome, but the Pro one is even better! With Pro version you will get Unlimited Data, Unblock over 60 Countries and 110 Cities, Config Generator (OpenVPN, IKEv2, SOCKS5), and full protection from R.O.B.E.R.T.
For your information, Windscribe is one of the best VPN services in the category Free Audit, Value Audit and Overall Audit in BestVPN.com Awards 2019 (Read the White Paper here). You totally can believe in Windscribe (100% no logs).
And about R.O.B.E.R.T, it's an advanced DNS level blocker that protects you from Malware, Ads and Trackers, Social tracking, Porn, Gambling, Fake News, Clickbait and Cryptominers. Read more about R.O.B.E.R.T.
Anyway, Windscribe helps you:
- Stop tracking and browse privately: Governments block content based on your location. Corporations track and sell your personal data. Get Windscribe and take back control of your privacy.
- Unblock geo-restricted content: Windscribe masks your IP address. This gives you unrestricted and private access to entertainment, news sites, and blocked content in over 45 different countries.
- Take your browsing history to your grave: Protect your browsing history from your network administrator, ISP, or your mom. Windscribe doesn't keep any logs, so your private data stays with you.
- Stop leaking personal information: Prevent hackers from stealing your data while you use public WIFI and block annoying advertisers from stalking you online.
- Go beyond basic VPN protection: For comprehensive privacy protection, use our desktop and browser combo (they're both free).
Windscribe also supports Chrome browser, Firefox browser, Opera browser, Smart TV, Routers, Android, iOS, BlackBerry, Windows OS, Mac OS X and GNU/Linux OS, you name it.
You can install Windscribe on Ubuntu, Debian, Fedora, CentOS, Arch Linux and their based distros too.
But to install and safely use Internet through Windscribe, you must sign up an account first. If you already have an account then let's get started.
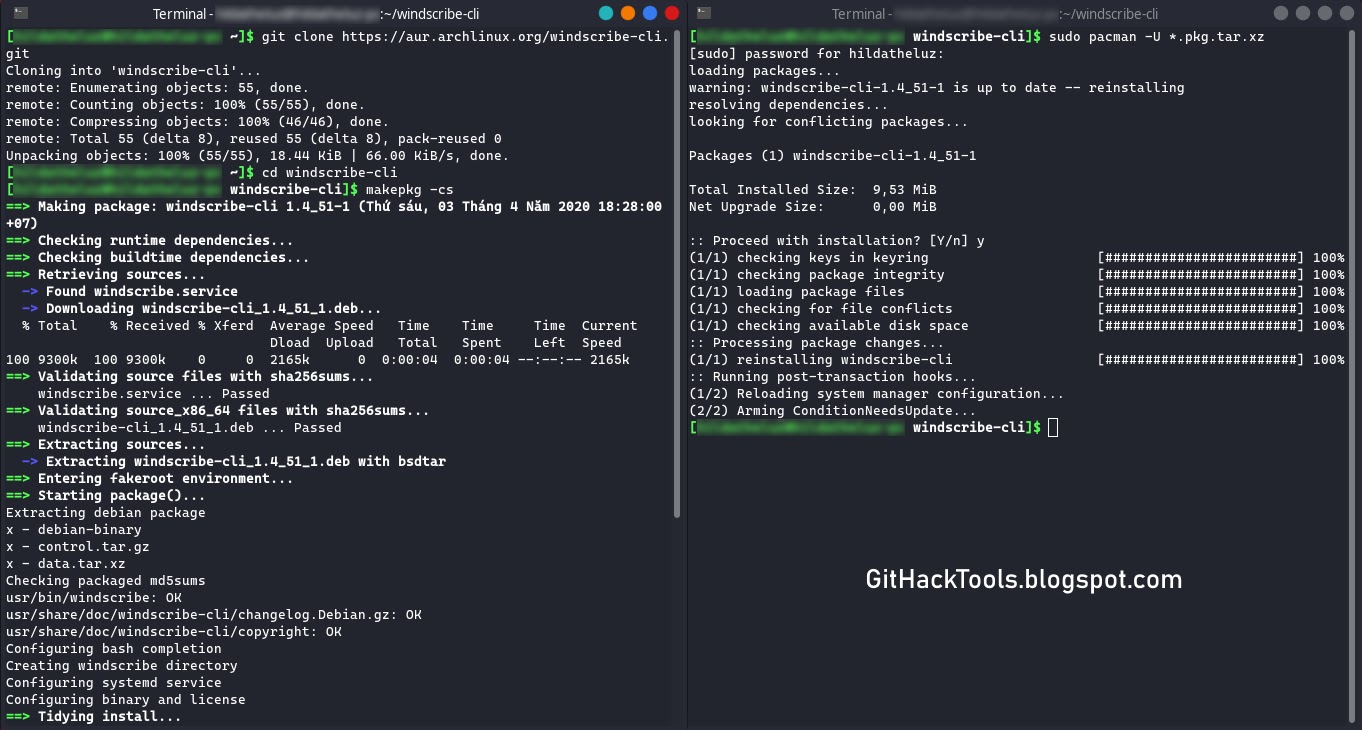
How to install Windscribe on Arch and Arch-based distros?
First, open your Terminal.
For Arch Linux and Arch-based distro users, you can install Windscribe from AUR. Run these commands without root to download and install Windscribe on your Arch:
For other distro users, go to VPN for Linux - Windscribe choose the binary file that compatible with your distro (
.DEB for Debian and Ubuntu based, .RPM for Fedora and CentOS based) and then install it.dpkg -i [Windscribe .DEB package]
rpm -ivh [Windscribe .RPM package]Or you can scroll down to Pick Your Distro, click to the distro version you use, or click to the distro version that your distro is based on and follow the instructions.
Now enter these commands to auto-start a and log in to Windscribe.
Enter your username and password and then you can enjoy Windscribe's free VPN service.
How to use Windscribe on Linux?
This is Windscribe list of commands (
windscribe --help):If you want Windscribe to chooses the best location for you, use
windscribe connect best.But if you want to choose location yourself, here is the list of Windscribe's locations:
*Pro only
Example, i want to connect to "Los Angeles - Dogg", i use
windscribe connect Dogg.If you want to stop connecting through Windscribe use
windscribe disconnect.For some reasons, you want to log out Windscribe from your device, use
windscribe logout.I hope this article is helpful for you 😃
More information
Top System Related Commands In Linux With Descriptive Definitions
Commands are just like an instructions given to a system to do something and display an output for that instruction. So if you don't know how to gave an order to a system to do a task then how it can do while you don't know how to deal with. So commands are really important for Linux users. If you don't have any idea about commands of Linux and definitely you also don't know about the Linux terminal. You cannot explore Linux deeply. Because terminal is the brain of the Linux and you can do everything by using Linux terminal in any Linux distribution. So, if you wanna work over the Linux distro then you should know about the commands as well.
In this blog you will get a content about commands of Linux which are collectively related to the system. That means if you wanna know any kind of information about the system like operating system, kernel release information, reboot history, system host name, ip address of the host, current date and time and many more.
Note:
If you know about the command but you don't have any idea to use it. In this way you just type the command, then space and then type -h or --help or ? to get all the usage information about that particular command like "uname" this command is used for displaying the Linux system information. You don't know how to use it. Just type the command with help parameter like: uname -h or uname --help etc.uname
The "uname" is a Linux terminal command responsible of displaying the information about Linux system. This command has different parameter to display a particular part of information like kernel release (uname -r) or all the information displayed by typing only one command (uname -a).uptime
This command is used to show how long the system has been running and how much load on it at current state of the CPU. This command is very useful when you system slows down or hang etc and you can easily get the info about the load on the CPU with the help of this command.hostname
The "hostname" is the the command in Linux having different parameters to display the information bout the current host which is running the kernel at that time. If you wanna know about the parameters of hostname command then you just type hostname --help or hostname -h to get all the info about the command and the usage of the command.last reboot
The "last reboot" is the command in Linux operating system used to display the reboot history. You just have to type this command over the Linux terminal it will display the reboot history of that Linux system.date
The "date" is the command used in Linux operating system to show the date of the day along with the current time of the day.cal
The "cal" command in Linux used to display the calendar which has the current date highlighted with a square box along with a current month dates and days just like a real calendar.w
The "w" is the command used in Linux distro for the sake of getting the information about current user. If you type this command it will display who is online at the time.whoami
The "whoami" is the command in Linux operating system used to show the information that who you are logged in as. For example if you are logged in as a root then it'll display "root" etc.finger user
The "finger user" is the command used in Linux distribution to display the information about user which is online currently over that Linux system.Continue reading
Suscribirse a:
Comentarios (Atom)